How Aikido helps in securing your Codebase!
You have programmed the whole system, Cool! But have you checked it?
With a rise in multiple SaaS startups growing around the world, companies are in more need of solutions that can help them in making their systems secure.
As a result, we have seen a good number of organizations emerging, which provide security testing for your codebase hosted on GitHub/GitLab, in containers, or any other remote place possible.
In this article, we are going to explore Aikido Security.
Aikido Security is a developer-friendly platform designed to automate application security throughout the entire software development process. Aikido combines various techniques like code analysis, dependency scanning, and cloud posture management. Aikido Security aims to simplify application security for developers by prioritizing real threats, reducing false alarms, and making security a seamless part of the development workflow.
How do they do it, and how can you try them out? Let's explore in this article!
Getting started with Aikido!
Go to Aikido Security website at https://www.aikido.dev/.
Click on 'Login' or 'Signup' with your account. I am using GitHub here for ease in the demo.
Grant the relevant permissions and log in to the dashboard.
Connect a workspace to which you want to scan and try out Aikido for how it reports vulnerabilities. Don't have a repository where you want to see results? No worries, you can check out a recently created collection of sample vulnerable code which should be identified by Bandit.
Link to the repository: https://github.com/anshuman-dev/try_aikido.
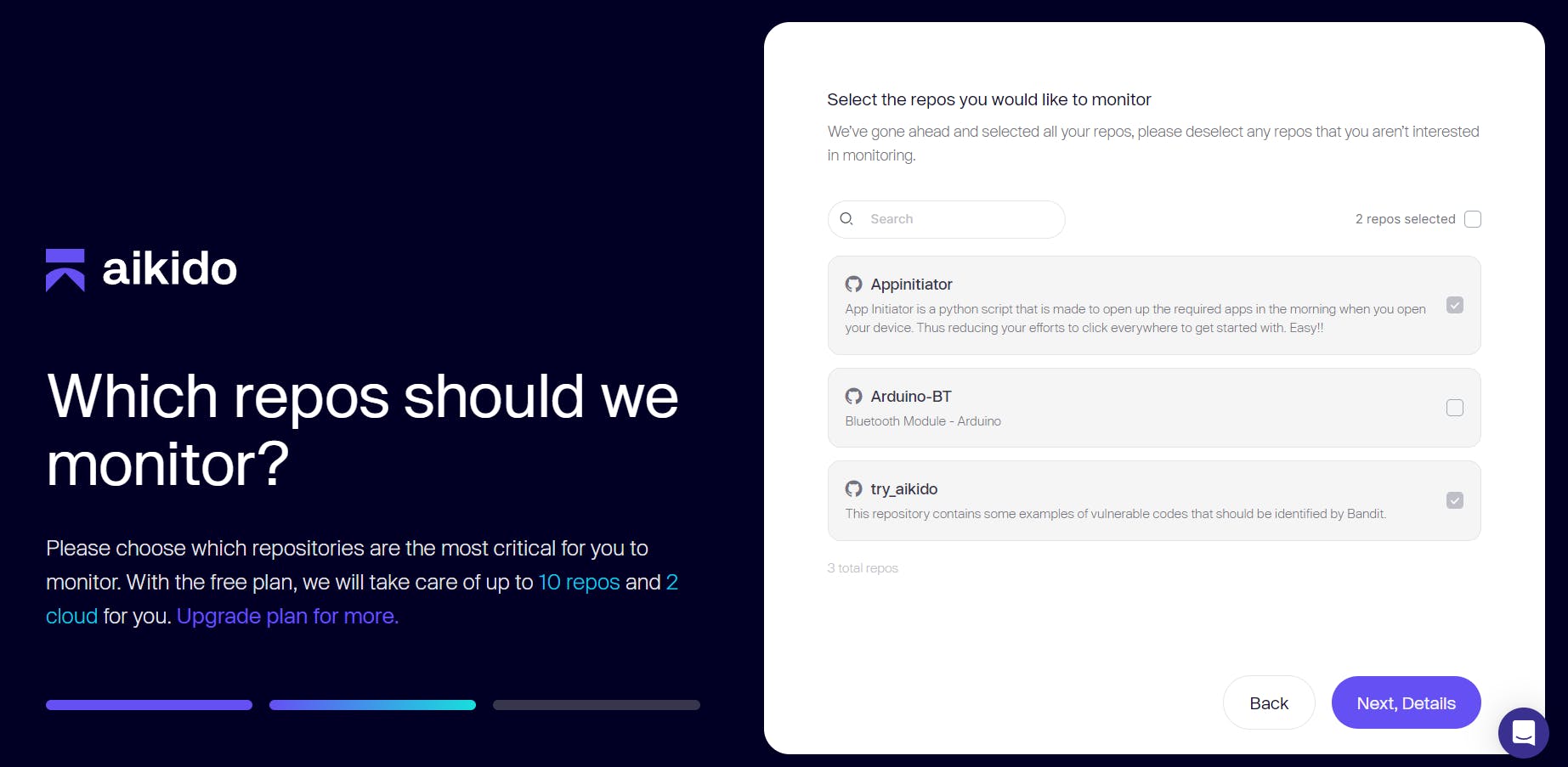
After connecting your workspace on Aikido Security, you will be required to select the repositories over which Aikido can perform vulnerability checks.
AND THAT'S IT! VOILÀ!
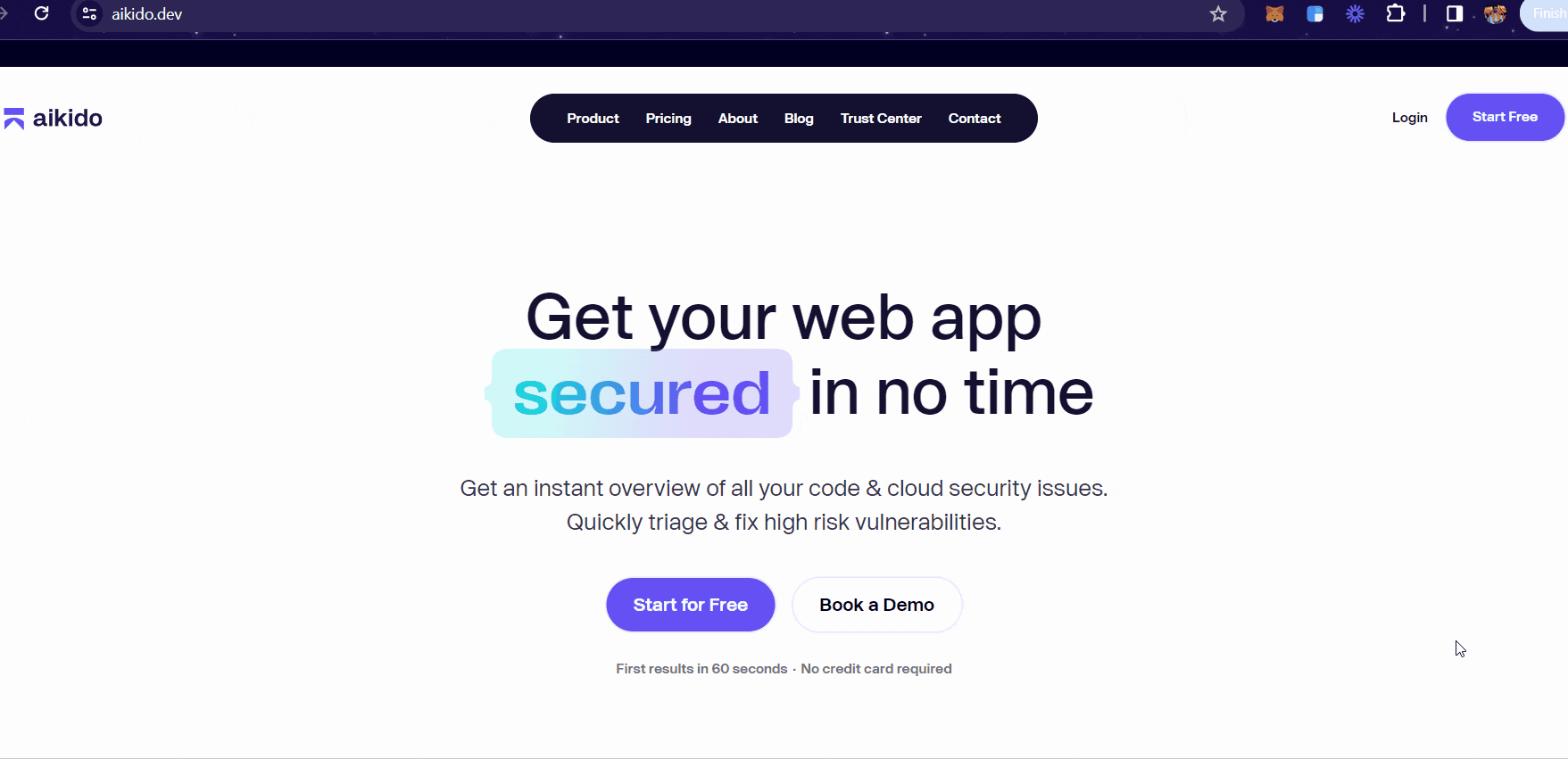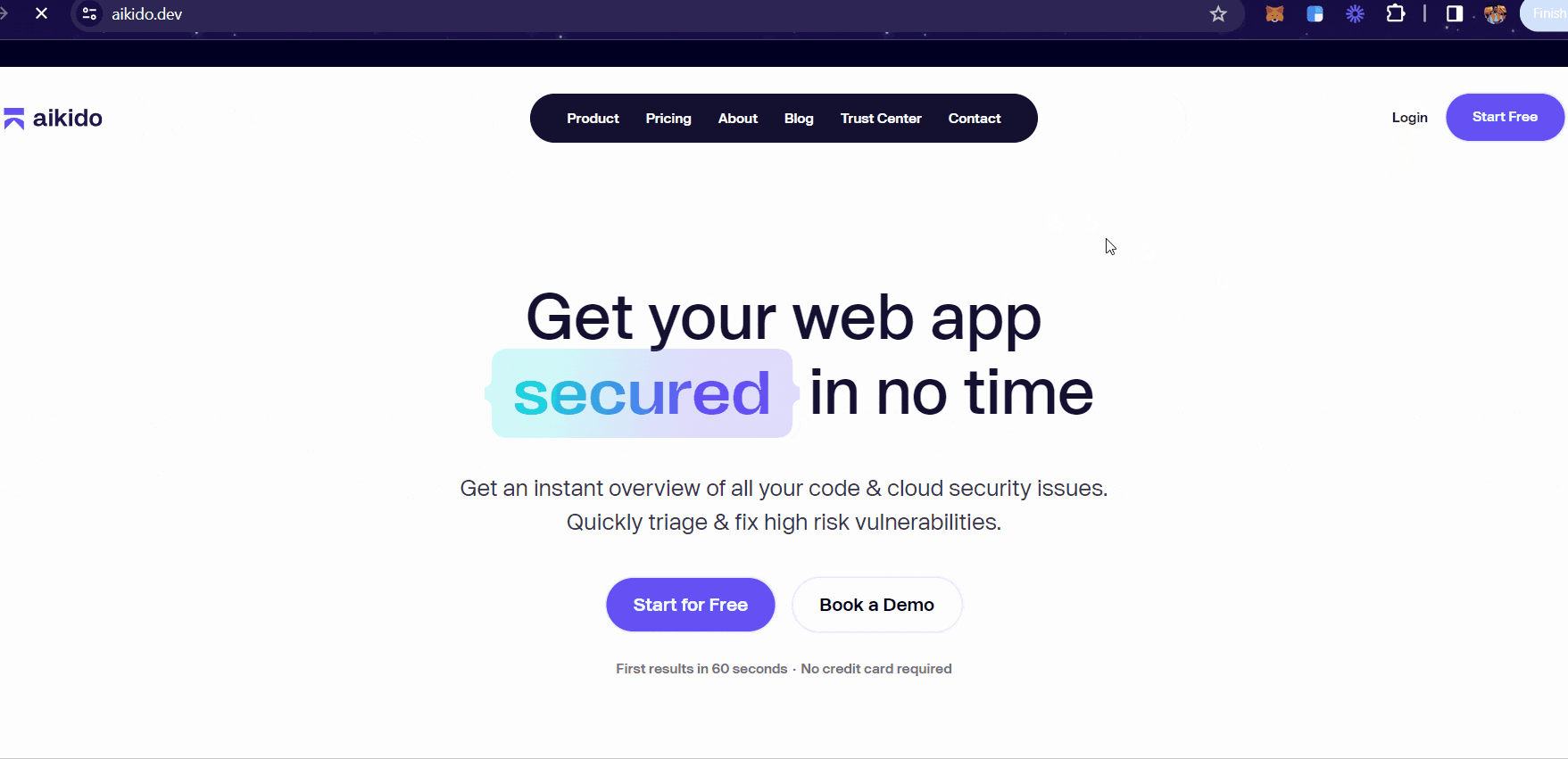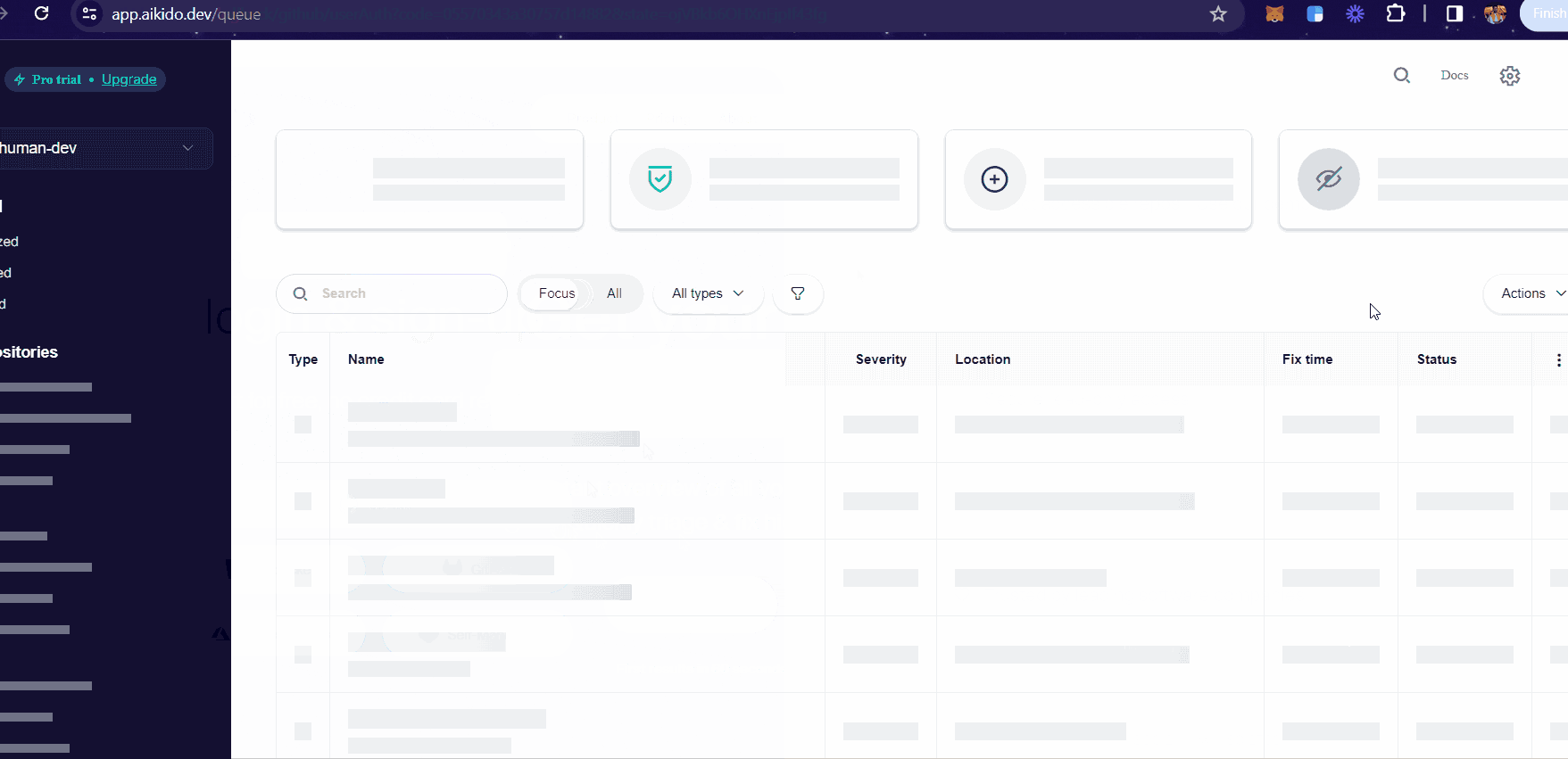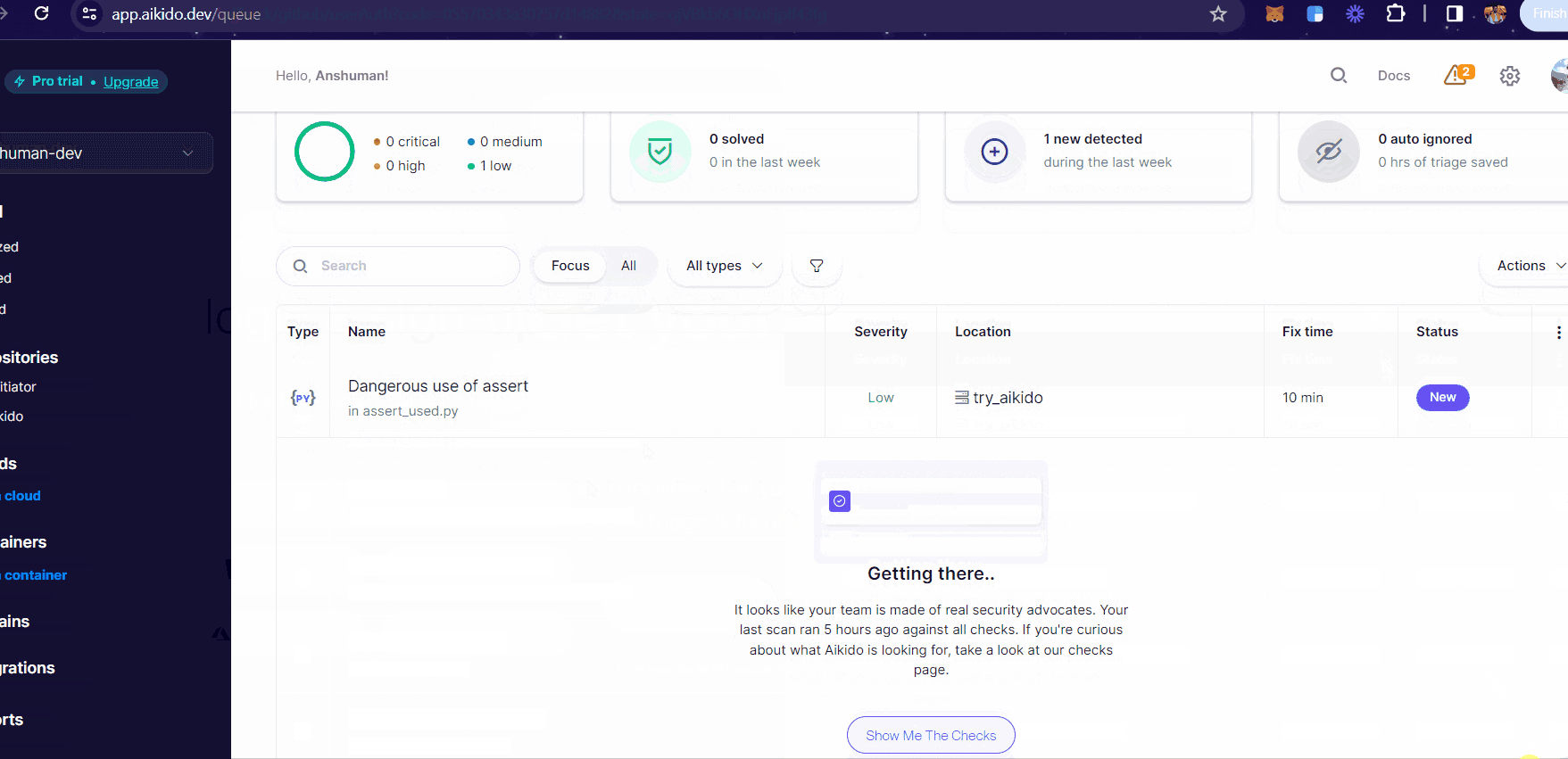
You can see the checks performed by Aikido on your repository on your Dashboard.
Let's check the analysis!
The table on the dashboard presents you with the following fields:
Type: Shows the language in which the code is written.
Name: A one line description of the vulnerability found.
Severity: What's the level of the risk?
Location: Where is the vulnerability found - which repository?
Fix Time: Estimated time to fix the vulnerability found.
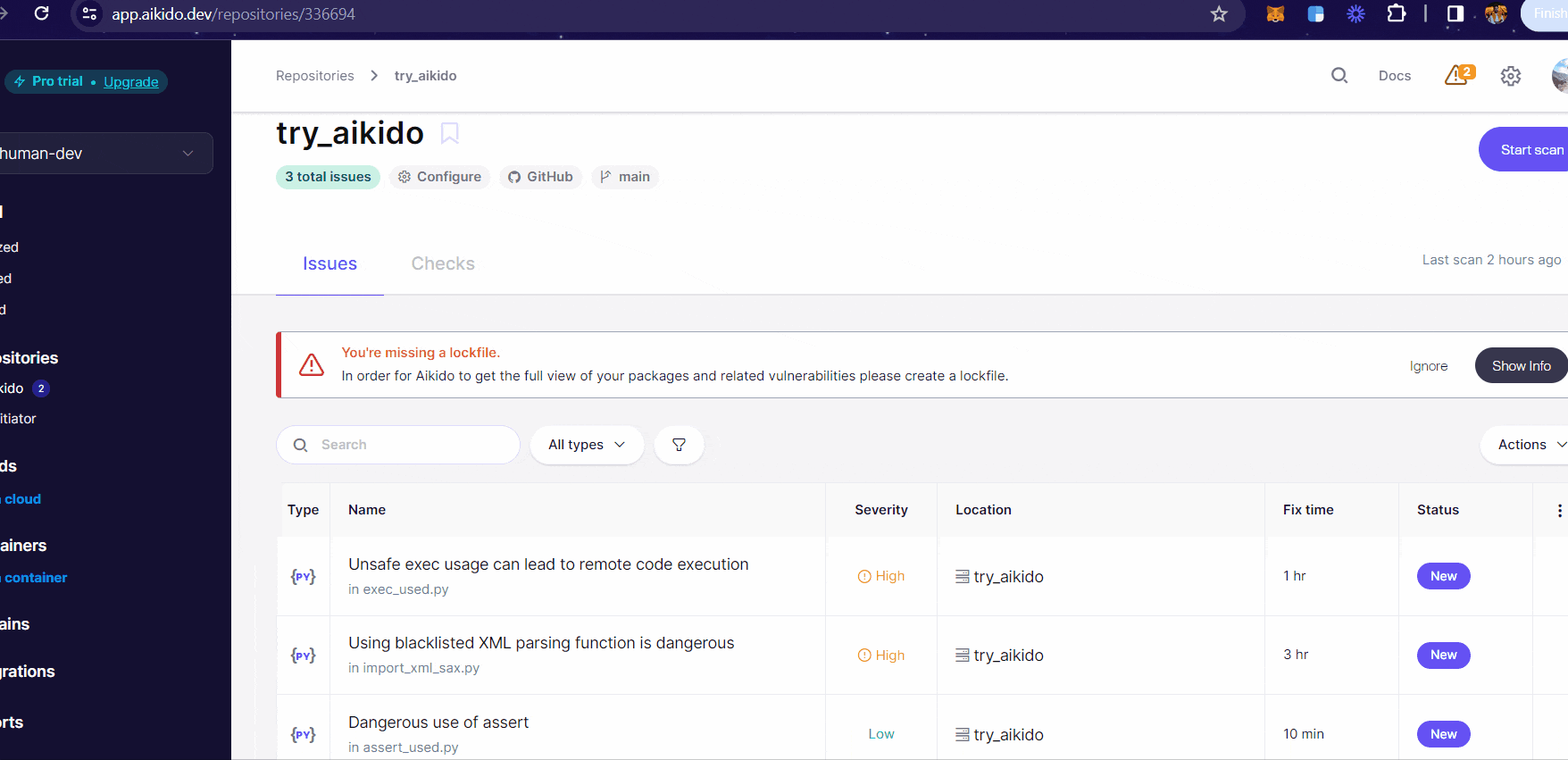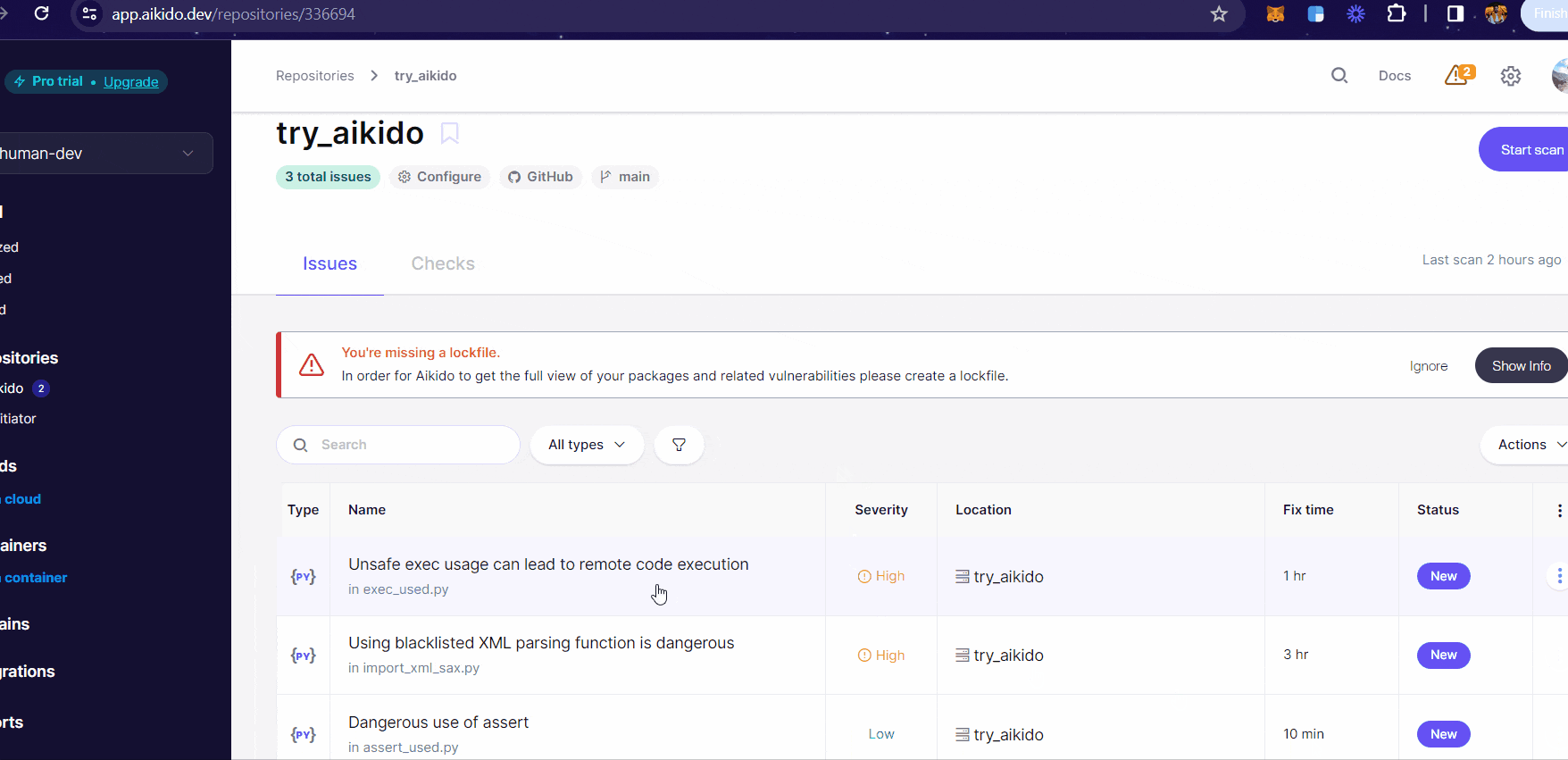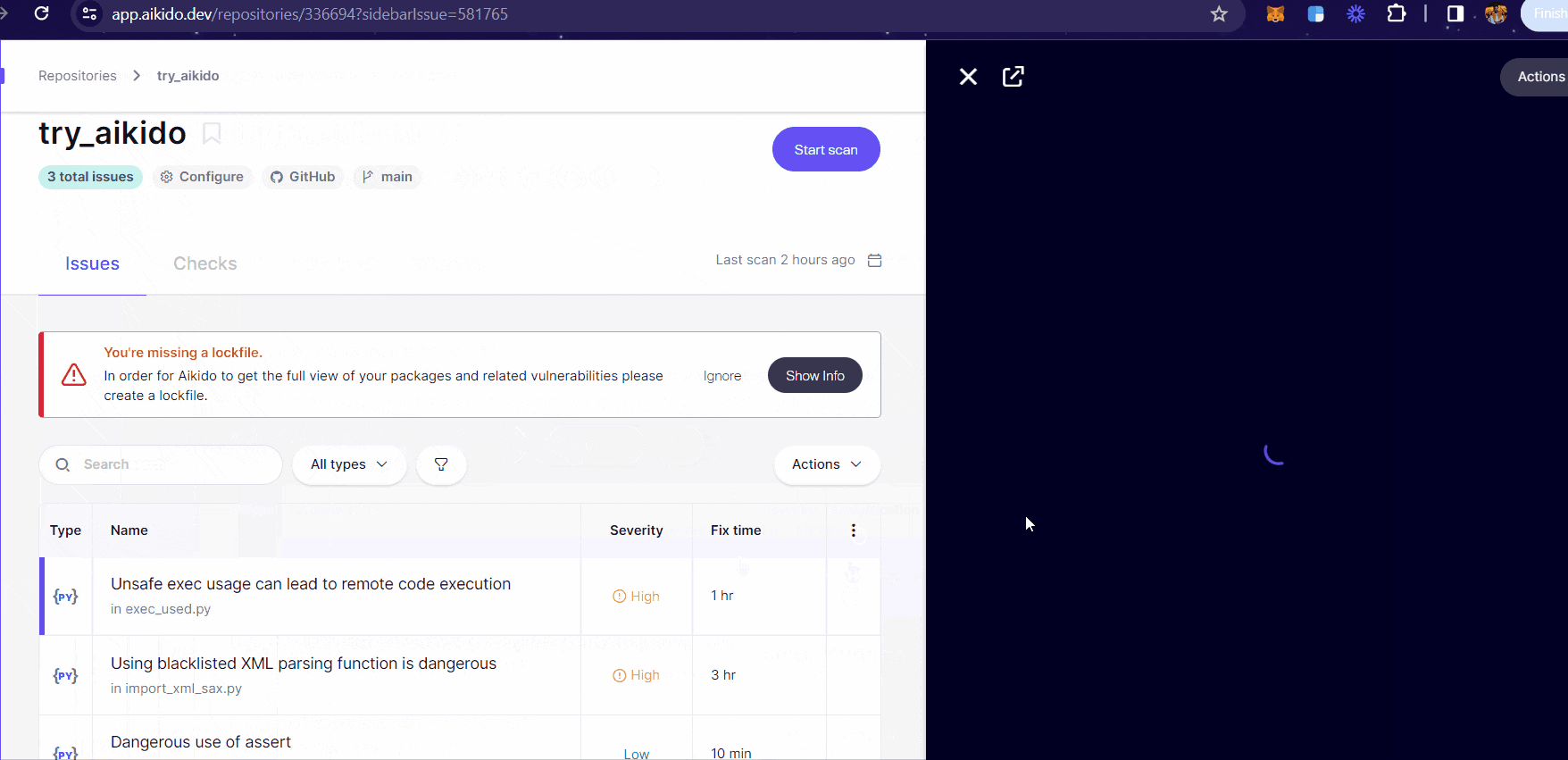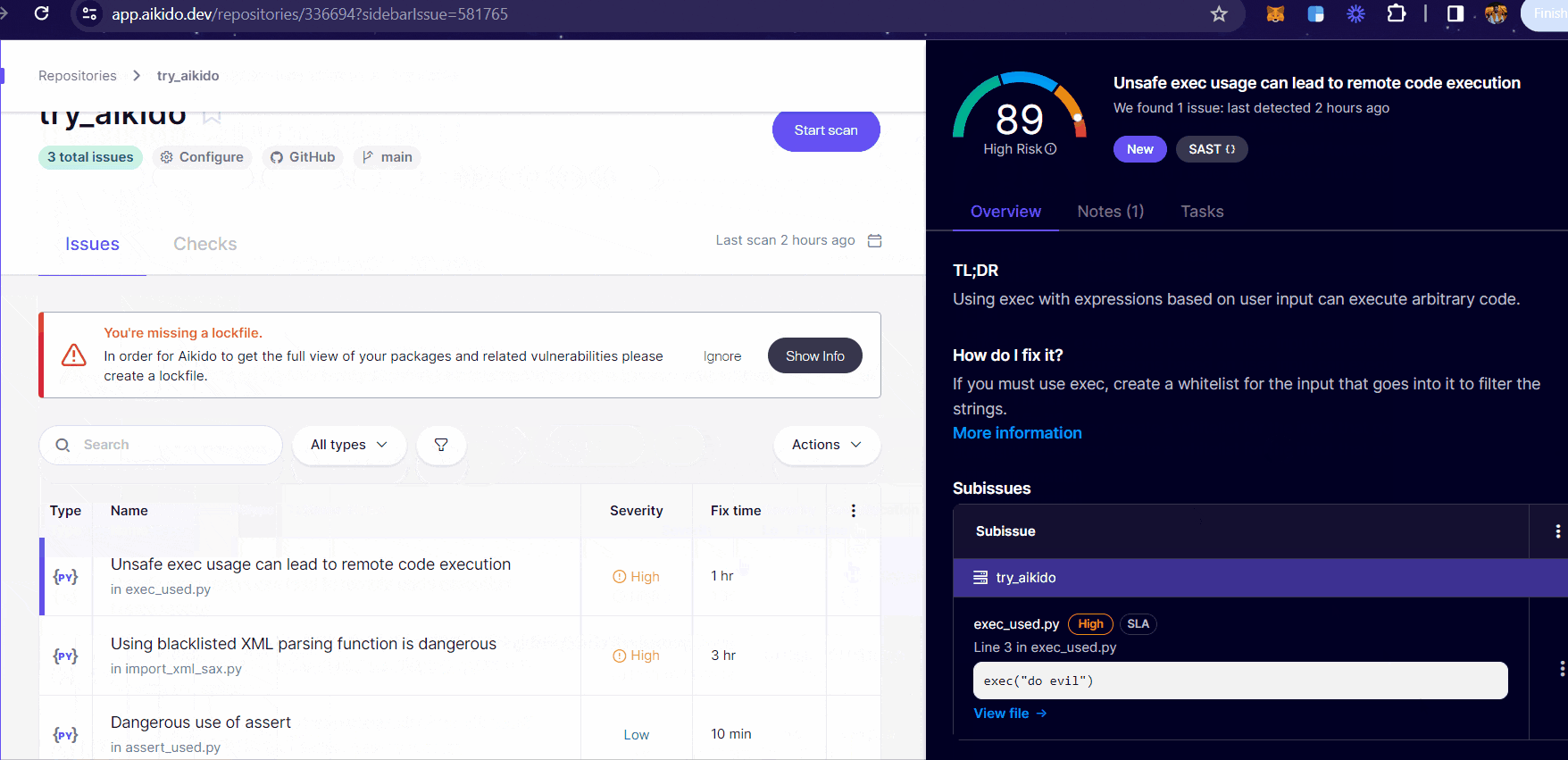
On clicking upon a vulnerability reported in the dashboard, you can look into specific details and perform several actions such as:
You can check the overview section providing a detailed breakdown of the issue found.
One can always track the specific LOC where the vulnerability has been found.
Add Notes about the vulnerability found and add a visibility tracker for who should be able to see them.
Create tasks to be associated with this issue and so much more!
What's next?
Try out the platform here: https://www.aikido.dev/.
You can also check out the Getting Started option at the bottom left to get a complete overview of the platform.
Additionally, checkout their Developer Docs here for you to get started on using the platform seamlessly: https://help.aikido.dev/en/.