Application Security Basics - SAST, DAST and more!
Learn about basic software tools and terminologies - CWE, CVE, SAST and DAST.
Ever wondered what it means when you read the headlines or hear -
"Hackers attacked XYZ systems! Possibility of a data breach!"
Of course, this doesn't mean attacking using arrows or weapons but how do they do this? Hackers or more specifically Black Hat hackers can find vulnerabilities in your codebase. These vulnerabilities are most likely some depreciated libraries or functions which can easily be manipulated to harm the system.
So how do companies prevent themselves from writing such code which is vulnerable to attacks?
There are many ways to go about this. In this article we will be discussing some basic application security methodologies about this, i.e., SAST - Static Application Security Testing, DAST - Dynamic Application Security Testing, CWE and CVE.
CWE - Common Weakness Enumeration
Common Weakness Enumeration is a list being maintained by application security community that enlists security vulnerabilities. A weakness, according to CWE website is defined to be a condition in a software, firmware, hardware or service that, under certain circumstances has the potential to add vulnerabilities in our application.
The list of CWE is curated to educate software developers and researchers. This education is meant to develop applications that introduction of these vulnerabilities can be prevented at the initial stage.
Weaknesses listed down in CWE are scores - Common Weakness Scoring System(CWSS) for consistently prioritizing software weaknesses. The following image provides a brief overview of the scoring system of CWEs.
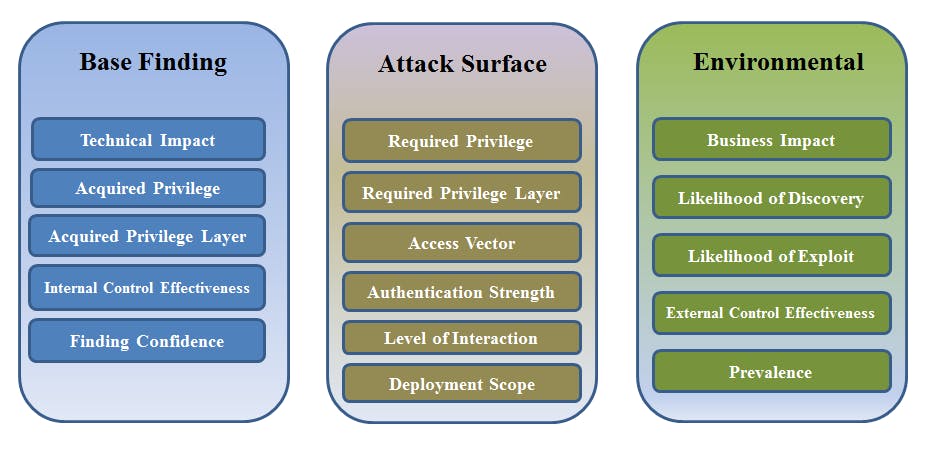
CVE - Common Vulnerability Enumeration
CVE comes under a CVE Program which also focuses on identification, defining and then ultimately listing down all the publicly disclosed Vulnerabilities. For every vulnerability that is found, it is recorded in a CVE Record. Primarily this information is used by security professionals and software developers to coordinate their discussion and efforts of solving and preventing software vulnerabilities.
Every possible vulnerability which has been detected is assigned a CVE ID, which can be explored through the CVE List.

Let's now dive into the frameworks used, in which we develop the technologies to build secure-vulnerability-free applications.
SAST - Static Application Security Testing.
SAST encompasses a set of technologies that are curated to go through a given codebase and detect possible vulnerable points in it. Applications providing SAST service analyze the entire given application statically.
SAST is typically known for White box testing. In a given software architecture SAST is performed when all pieces of code are put together and sent for ultimate testing. There are various ways to perform SAST on your application. Softwares like GitLab provide SAST service in their integrated CI/CD pipeline and a visual dashboard as well showing all the detected vulnerabilities with their Severity Level.
To add, we have tools like Flawfinder for C programming language and Bandit for Python programming language which can be used to perform SAST on the written specific programming languages.
Recently, I stumbled upon Semgrep during my internship with GitLab which is an amazing, simple yet powerful tool for detecting code vulnerabilities. Using Semgrep you can write powerful rules in plain English using YAML, but that's a post for another day. Don't feel like this:

Let's learn then what DAST is.
DAST - Dynamic Application Security Testing.
The word Dynamic here makes all the difference. Deploying your application into new environments invites new software vulnerabilities and attacks. To deal with such instances, DAST comes into place.
DAST can be done manually or can be automated as well. Tools under this can detect conditions indicative of security vulnerabilities in the running state of the application. Currently, a lot of DAST solutions available simply test the HTML and HTTP endpoints. However, companies such as GitLab again can provide dynamic and better solutions by providing a comprehensive analysis of your deployed architecture.
SUMMARY

Thus, companies either use or create their own Static/Dynamic tools to protect their codebase from security attacks. Using the information of prior discovered vulnerabilities through CVE and CWE, companies set up the infrastructure for developing vulnerability-free applications.
Hope this article was informative.
Cheers!🚀